AI Agent Permissions 2026: How to Design Least-Privilege Tool Access Without Killing Automation
Why permissions are the real “agent safety layer”
Most teams treat agents like chatbots. Then they connect them to CRM, email, calendar, Drive, billing, databases, and internal admin panels.
That’s not a chatbot anymore. That’s an operator with hands.
If you don’t design permissions properly, your agent will eventually:
- access data it shouldn’t
- take actions it shouldn’t
- leak information across clients
- become impossible to audit
- create a nightmare when something goes wrong
The fix is not “better prompts.” It’s least privilege by design.
The difference between authentication and authorization
This sounds basic, which is why humans ignore it until they’re in trouble.
Authentication
Who is calling the tool?
Example: is this “Sales Agent” or “Support Agent” or “Admin Agent”?
Authorization
What is that caller allowed to do?
Example: can it read contacts, edit deals, send emails, issue refunds, export data?
Agents need both, and they need them per workflow, not “one API key to rule them all.”
The 5 permission mistakes that break production agents
1) Shared keys across everything
One key used for all agents, all clients, all workflows.
Result: one mistake becomes a full-system breach.
2) God-mode tool access
Agent can read and write everything because “it’s easier.”
Result: easy now, catastrophic later.
3) No tenant isolation
Multi-client setup with weak boundaries.
Result: cross-client data bleed, which is instant death for an agency.
4) Actions not separated by risk
Reading is treated the same as sending and deleting.
Result: agent does irreversible actions too easily.
5) No audit trail
You can’t answer: who did what, when, and why.
Result: you can’t debug, you can’t prove compliance, you can’t defend decisions.
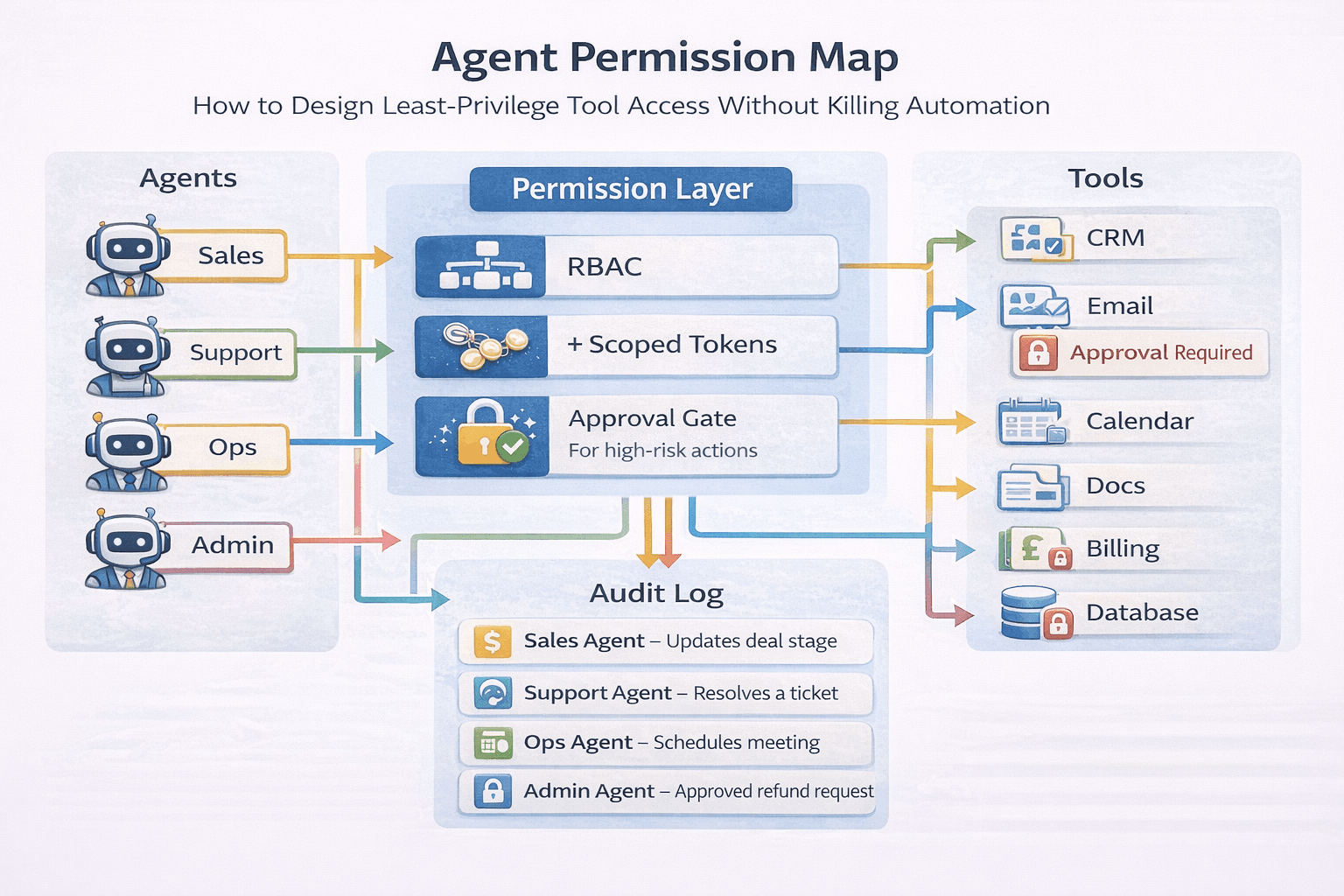
The least-privilege model that actually works
You want a structure like this:
Agent identity
Each agent gets its own identity:
- Sales Agent
- Support Agent
- Research Agent
- Content Agent
- Admin Agent
No identity, no control.
Role-based permissions
Define roles that map to real business responsibilities:
- Sales: read leads, update deal stage, draft emails, request send approval
- Support: read tickets, propose responses, update status, escalate
- Ops: read invoices, reconcile fields, create tasks, never send money
- Admin: limited, gated, audited, human-approved actions only
Tool-level scopes
For each tool, define allowed operations:
- read only
- write only for specific fields
- delete never
- export never
- send only with approval
- update only within tenant boundary
Tools should reject unauthorized actions server-side, not “politely ask the model to behave.”
The “approval gate” for high-risk actions
Even with perfect permissions, you still need gating for actions that can harm the business.
Always gate:
- sending external emails
- posting publicly
- billing changes
- refunds
- permission changes
- deletions
- exports
- anything that touches payroll, HR, legal, or medical content
Low-risk actions can be automatic. High-risk actions go through a queue.
This keeps automation fast without being reckless.
How to manage secrets without leaking them everywhere
Agents don’t need to “know” secrets. Systems do.
Good practice:
- keep secrets outside the model context
- use short-lived tokens instead of permanent keys
- rotate credentials on schedule
- scope tokens per tenant and per workflow
- store secrets in a proper secret manager, not config files and vibes
- log access without logging the secret
If your agent can print the key, you already lost.
Multi-tenant agency setup: how to not get cooked
If you run multiple clients, isolation is mandatory.
You need:
- one tenant boundary per client
- separate credentials per tenant
- separate storage per tenant where practical
- strict checks that every tool call includes tenant_id
- hard server-side enforcement that blocks cross-tenant access
Do not rely on “the agent will remember which client this is.” It won’t.
The permission blueprint for real agent systems
A production pattern looks like:
- Request comes in with tenant_id and workflow_id
- Router selects agent identity and role
- System issues scoped token for that tenant and that workflow
- Agent can call only approved tools with approved operations
- High-risk actions require approval token from a human
- Everything writes to an audit log (who, what, when, outcome)
This is how you scale agent autonomy without scaling risk.
The agency offer this enables
This is premium work because it’s hard and businesses fear it.
You sell:
- agent identity and role design
- tool permission mapping
- gated action flows
- tenant isolation architecture
- auditing and compliance logging
- ongoing ops and updates as systems evolve
Clients don’t just want automation. They want automation they can trust.
Agents with bad permissions are a liability generator.
Agents with least privilege become a real operational asset.
If you want “AGI vibes” in production, it starts with boring grown-up access control.
Neuronex Intel
System Admin